How to Choose the Best Door Access Control System to Secure Your Office Spaces

In today’s fast-paced office environments, security is an all-important necessity for maintaining operational integrity. Protecting sensitive data, assets, and personnel requires robust, flexible security solutions. As such, door access management systems are needed to manage entry across office spaces. They do more than just restrict access—they streamline and secure the flow of authorised personnel.
With offices of all sizes and evolving technologies, choosing the right door access control system is a strategic decision. Whether it’s traditional keycard access, biometric locks, or smart systems, the right choice should align with security goals and operational needs. This guide will help businesses navigate door access management systems, covering system types, selection factors, installation and maintenance, compliance, and future-proofing. With these insights, companies can enhance security, improve efficiency, and stay ahead in an ever-changing technological landscape.

Part 1: Understanding Door Access Management Systems
1.1 What Are Door Access Management Systems?
Door access management systems are advanced security solutions designed to control and monitor entry to various office areas. Their primary purpose is to enhance security by ensuring that only authorised individuals can access specific zones, such as general workspaces, high-security data centres, or executive meeting rooms.
These systems typically include several key components:
- Locks: The physical mechanism securing the door.
- Access Credentials: Access cards, PIN codes, or biometric data (fingerprints or facial recognition) are used to authorise entry.
- Biometric Readers: Devices that authenticate identity using unique physical traits.
- Control Panels and Software: The system’s central hub, which validates credentials, stores data, and allows customisable access settings.
In action, these systems streamline entry by granting access through pre-approved credentials. Moreover, they maintain detailed logs of all activities, supporting security audits or investigations when necessary.
1.2 The Role of Security in Modern Office Environments
Security is no longer just a nice-to-have—it’s a requirement for today’s fast-paced workspaces. Here’s why door entry systems are vital for contemporary businesses:
-
Protecting Valuable Assets:
Modern offices store sensitive data, intellectual property, and high-value equipment. Door security systems for offices prevent unauthorised access, keeping these critical assets safe.
-
Ensuring Workplace Safety:
Restricting access to authorised personnel improves safety by reducing the risk of intruders or unauthorised individuals in the workplace.
-
Meeting Regulatory Compliance:
With increasing data protection and workplace safety regulations, door access solutions help businesses comply with standards like GDPR, PDPA or ISO, especially when handling sensitive data.
-
Streamlining Operations:
Physical keys are prone to loss, theft, or duplication, creating vulnerabilities. Controlled door access systems eliminate these issues with secure, digital alternatives that are easier to manage.
-
Enabling Data-Driven Monitoring:
Detailed entry and exit logs allow businesses to track who accessed specific areas and when, improving security and supporting audits or investigations if needed.
As businesses grow and evolve, integrating reliable door access management systems becomes critical to maintaining a robust, efficient, and future-proof security framework.

Part 2: Types of Door Access Management Systems
2.1 Keycard and RFID Systems
Keycard and RFID door access systems are some of the most widely used security solutions in office environments. They balance simplicity, affordability, and scalability, making them a popular choice for businesses of various sizes.
Keycard Access Solutions
Keycard systems use cards embedded with magnetic stripes or chips that store access credentials. To gain entry, users simply swipe or tap their card on a reader, which then validates the credentials and grants access.
RFID Security Systems
RFID (Radio Frequency Identification) systems take things a step further by using wireless technology for authentication. RFID cards or tags contain small chips and antennas that communicate with readers via radio waves, allowing users to gain access by simply tapping or holding their card near the reader for contactless entry.
2.1.1 Advantages and Disadvantages
Advantages
- Ease of Use: Access is quick and hassle-free with a simple swipe or tap, making the system user-friendly.
- Scalability: As your businesses grow, these systems can easily accommodate more users and access points without requiring major infrastructure changes.
- Cost-Effective: Keycard and RFID systems are more affordable than advanced biometric options, making them an ideal choice for businesses with budget constraints.
Disadvantages
- Security Risks: Lost or stolen cards pose significant security risks, and keycards are vulnerable to duplication, compromising system integrity.
- Wear and Tear: Magnetic stripes on keycards are prone to degradation over time, leading to errors and the need for replacements.
- Limited Data Capacity: RFID cards have limited storage capacity, which could restrict their functionality for complex security requirements.
2.1.2 Use Cases for Keycard and RFID Systems in Office Settings
Keycard and RFID systems are highly versatile and can be used in various office scenarios:
- General Office Access: These systems are widely used for controlling entry to main entrances, employee workspaces, and shared facilities.
- Parking Facilities: RFID cards can manage automated and secure access to office car parks.
- Meeting Rooms: These systems can be installed to limit access to conference rooms, ensuring that sensitive discussions are only accessible to authorised personnel.
- Visitor Management: Temporary access cards can be issued to visitors, providing controlled access without compromising overall office security.
2.1.3 Key Considerations for Implementation
When integrating keycard or RFID systems, consider these factors:
- System Compatibility: Ensure the new system works with existing security infrastructures, such as CCTV or alarm systems.
- Card Management: Set clear protocols for issuing, tracking, and deactivating cards to prevent unauthorised access.
- Security Protocols: Implement measures like encryption or advanced authentication methods to avoid cloning or duplication of access cards.
- Budget Planning: Factor in both initial setup costs and long-term expenses, including card replacements and system upgrades.
Keycard and RFID systems provide a practical, cost-effective solution for improving office security. However, careful planning and ongoing management are necessary to fully leverage their benefits while minimising potential vulnerabilities.

2.2 Biometric Door Access
Biometric door access facilities take office security to the next level by using unique biological traits for precise identification and authentication. Unlike conventional methods that rely on cards or PINs, biometric systems offer exceptional security and convenience, making them ideal for modern office environments.
Biometric door locks authenticate individuals by recognising their distinct biological traits. Common methods include:
- Fingerprints
- Facial Features
- Iris Patterns
- Palm Vein Patterns
These traits are almost impossible to replicate, offering a high level of security for office spaces.
2.2.1 Fingerprint Door Lock
A digital door lock fingerprint system uses a scanner to capture a user’s fingerprint. This fingerprint is then compared to pre-stored templates in the system’s database, granting door access if there is a match.
Benefits
- High Security: Fingerprints are incredibly difficult to forge, providing top-tier security.
- Convenience: There’s no need for keys, cards, or PINs, eliminating the risk of lost or forgotten credentials.
- Speed: The authentication process is quick and seamless, allowing fast entry.
Applications
- Sensitive Areas: Ideal for safeguarding server rooms, R&D labs, and executive offices.
- Personalised Access: Limits access to specific individuals based on roles or security clearance.
- Sensitive Areas: Ideal for safeguarding server rooms, R&D labs, and executive offices.
- Personalised Access: Limits access to specific individuals based on roles or security clearance.
2.2.2. Facial Recognition
Facial recognition door locks use a camera to capture a person’s facial features, such as the distance between the eyes, the nose’s shape, and the mouth’s contours. These features are then compared to stored data to confirm the user’s identity.
Benefits
- High Security: Advanced algorithms make bypassing the system with fake images or masks nearly impossible.
- Contactless Operation: No physical contact is needed, making it ideal for hygiene-conscious workplaces, such as healthcare environments.
- Ease of Use: It eliminates the need to carry physical credentials or remember passwords, enhancing user experience.
Applications
- High-Traffic Areas: Effective in managing central office entrances where frequent access is needed.
- Hygienic Environments: Preferred for spaces like clinics or food manufacturing facilities, where cleanliness is a priority.
2.2.3 Iris and Palm Vein Scanning
- Iris Scanning: An infrared camera captures the intricate patterns in the iris, unique to each individual.
- Palm Vein Scanning: Near-infrared light is used to detect palm vein patterns, which remain unchanged throughout a person’s life.
Benefits
- High Accuracy: Both methods offer exceptional precision, minimising false positives and negatives.
- Spoof-Resistant: Iris patterns and vein structures are nearly impossible to replicate, ensuring robust protection.
- Non-Intrusive: These contactless methods are non-invasive and help maintain hygiene.
Applications
- Top-Security Zones: Ideal for high-security areas like vaults or data centres.
- Hygiene-Critical Settings: Useful in environments such as laboratories or cleanrooms, where contactless solutions are required.
Biometric door access utilities offer a transformative approach to office security. By combining advanced technology with user-friendly features, they cater to diverse business needs, providing robust security without sacrificing convenience.

2.3 Smart and Automatic Access Management Systems
Incorporating smart and automatic door access solutions into modern office environments significantly boosts both security and operational efficiency. These advanced systems harness the power of IoT (Internet of Things), cloud platforms, and automation to offer flexible, scalable access management.
2.3.1 Overview of Smart Office Access Control Systems
Smart access control systems utilise IoT technologies to link with smart devices, providing centralised and sophisticated access control for office spaces.
Components
- Smart Locks: Secure locking mechanisms that communicate with authorised devices or credentials to grant access.
- Mobile Applications: Allow administrators to manage access remotely and monitor entry logs in real-time.
- Cloud-Based Platforms: Offer a user-friendly interface for controlling access, generating reports, and storing data.
Key Features and Benefits
- Remote Management: Administrators can adjust access permissions and monitor activity from anywhere using apps or web portals.
- Customisation: Permissions can be set based on individual roles or schedules, offering flexibility and targeted security.
- System Integration: Seamlessly integrates with other office systems like CCTV, alarms, and HVAC, providing unified security and operational control.
- Analytics: Delivers in-depth reports and analytics to identify trends, optimise security protocols, and enhance decision-making.
2.3.2 Automated Door Access Utilities
Advantages
- Hands-Free Operation: Automatic doors open smoothly for authorised individuals using credentials or sensors, providing greater convenience.
- Improved Efficiency: Great for high-traffic areas, they reduce delays and maintain a smooth flow of individuals in and out.
- Heightened Security: Automatic door access control systems ensure doors remain locked to unauthorised users, bolstering office security.
Ideal Scenarios
- Busy Entrances: High-volume areas like main office doors or reception areas benefit from hands-free, efficient access.
- Critical Zones: Highly secure spaces such as data centres or executive offices require strict access management.
- Accessibility Compliance: Automatic doors meet accessibility standards, offering a secure and user-friendly solution for individuals with disabilities.
2.3.3 Integration with Other Smart Office Technologies
Seamless Connectivity
Intelligent door access facilities integrate effortlessly with existing office technologies:
- CCTV Cameras: Combines access control data with live video feeds for more effective monitoring.
- Alarm Systems: Triggers automatic alarms in the event of an unauthorised access attempt.
- Building Management Systems (BMS): Works alongside HVAC, lighting, and energy systems to enhance both security and energy efficiency.
Comprehensive Security Management
This interconnectedness allows for centralised monitoring and control of the entire office security ecosystem, streamlining processes and reducing administrative overheads.
Enhanced Situational Awareness
Real-time data sharing and analytics across integrated systems improve awareness of potential security threats, enabling swift, informed responses to incidents. Smart and automatic access control systems are indispensable for businesses seeking innovative, scalable, and user-centric solutions. By embracing these technologies, offices can strengthen security, improve accessibility, and build a future-ready infrastructure that evolves with their needs.
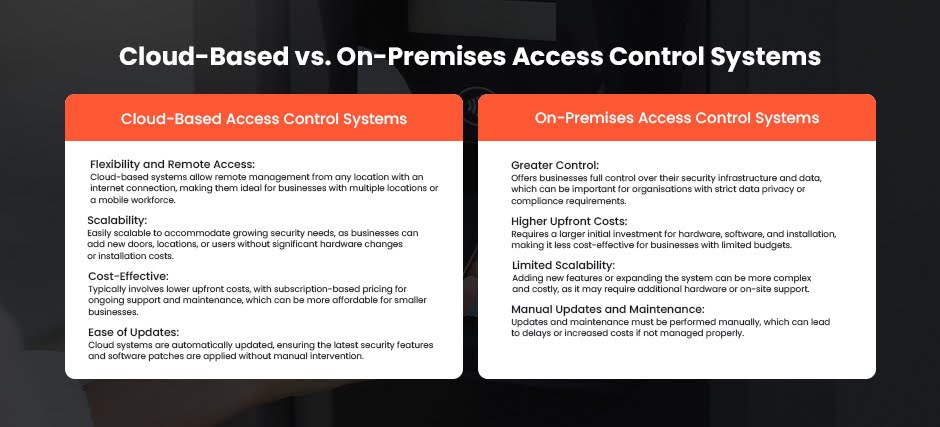
Part 3: Choosing the Right Door Control Systems
3.1 Assessing Your Office Needs
When it comes to selecting the right door access management solution, it begins with a clear understanding of the office’s unique requirements. A tailored approach ensures that the chosen system aligns with the organisation’s security, operational, and scalability goals.
3.1.1 Key Factors to Consider
Office Size
- Layout Complexity: A small office with a single entry point may only need a basic system. Meanwhile, larger spaces with multiple zones require advanced solutions to manage different access levels.
- Access Zones: Identify high-security areas like server rooms, storage spaces, or executive offices that demand stringent access controls.
Number of Employees
- User Volume: Larger teams benefit from systems that can handle high-capacity user databases, such as biometric or RFID-based solutions.
- Credential Management: Consider how access credentials will be issued, tracked, and deactivated for temporary staff, contractors, or visitors.
Required Security Level
- Sensitive Areas: High-risk zones, such as IT hubs or archives, may need more advanced systems, like biometrics, for added security.
- General Areas: Common zones like main entrances or parking facilities might only require scalable RFID or keycard solutions.
3.1.2 Importance of Scalability and Flexibility
Scalability
- Future Growth: Opt for a scalable system that can accommodate more users, devices, or locations without requiring a complete overhaul.
- Adaptability: Businesses with plans for expansion or restructuring benefit from systems that grow alongside them.
Flexibility
- Access Adjustments: Flexible systems support changes in access permissions as roles and responsibilities evolve.
- Customisation: Tailored configurations enable specific security measures for different departments or projects.
3.1.3 Determining the Best System According to Office Needs
1. Conduct a Needs Assessment
- Analyse the office’s operational workflow and identify security challenges. Involve primary stakeholders to ensure the system meets both current and future requirements.
2. Match Features to Requirements
- Evaluate the system based on its ability to integrate with existing infrastructure, such as CCTV or alarm systems. It’s also essential to consider user-friendliness so that employees can quickly get used to the new system.
3. Weigh Security and Convenience
- Advanced systems like biometric locks provide high security for sensitive areas but may require a larger investment. More basic solutions, such as RFID, offer a cost-effective approach to general access control and visitor management.
Taking the time to assess an office’s specific needs will not only optimise the investment but also ensure a secure, efficient, and adaptable workplace environment. The right system should strike the perfect balance between robust security, user convenience, and the flexibility to evolve with the business.

3.2 Installation and Maintenance Considerations
Proper installation and regular maintenance are critical to ensuring a door access control system operates efficiently and reliably. Understanding the process, budgeting effectively, and partnering with the right provider enables businesses to optimise system performance while minimising downtime.
3.2.1 Overview of the Office Security Systems Installation Process
Door access system installation requirements vary depending on the type of system chosen, such as biometric systems, RFID, or smart locks. Key aspects include:
- Physical Setup: This involves installing and wiring hardware components like access readers, control panels, and locks, ensuring that devices are securely mounted to prevent tampering and function smoothly.
- Software Configuration: Setting up the access management software includes registering credentials, assigning access levels, and integrating the system with existing technologies like CCTV or building management systems for enhanced functionality.
- Planning for Minimal Disruption: Businesses should coordinate installations during off-peak hours or complete in phases to avoid interrupting daily operations. Employees should also be notified about changes to access protocols in advance.
3.2.2 Costs Involved
Understanding the costs associated with installation and maintenance helps in effective budgeting. Below are some essential considerations:
- Initial Costs: These typically cover hardware (readers, control panels, smart locks), software licences for access control platforms or cloud systems, and professional services for installation and testing.
- Ongoing Expenses: These include routine maintenance (inspections, repairs, component replacements), software updates to enhance security and features, and periodic system audits to ensure compliance with security standards.
3.2.3 Installation Tips for Success
1. Clear Communication
Ensure that the service provider is fully informed of all requirements and timelines to avoid misalignments. Be clear about any unique needs, such as system integrations or customised access permissions.
2. Testing and Verification
After installation, conduct thorough testing to make sure all components are working as intended. Simulate different scenarios, such as emergency access or failed authentication, to test the system’s reliability.
3. Employee Training
Train employees on how to use the new system, including how to register credentials and troubleshoot minor issues.
3.2.4 Choosing a Reliable Service Provider
The right service provider plays a pivotal role in the successful deployment and maintenance of the system. Here’s how to find the right partner:
- Seek Recommendations and Reviews
Look for feedback from other businesses or industry peers who have used the provider’s services. Review online customer feedback to assess their reputation and reliability.
- Verify Credentials
Check that the provider has relevant certifications and experience with your chosen system type. They should also be familiar with local regulations and compliance requirements.
- Evaluate Support Services
Review service level agreements (SLAs) to understand the scope of ongoing support, including response times and maintenance schedules. Prioritise providers who offer 24/7 support to resolve critical issues quickly.
Planning for a smooth installation and maintaining the system over time ensures a secure, efficient, and hassle-free access control solution. Investing in the correct installation practices and service partnerships will maximise the system’s value while enhancing office security and operational convenience.

3.3 Securing Compliance and Future-Proofing
In the ever-evolving landscape of access control technology, businesses must comply with regulations while future-proofing their systems. Keeping up with local regulations, staying informed about technological advancements, and ensuring compatibility with existing office systems are all vital components in maintaining a secure, reliable, and scalable security solution.
3.3.1 Importance of Compliance with Local Regulations
In Singapore, businesses must make sure their access control systems align with local laws, building codes, and industry-specific standards. Compliance is not just about following the law but also safeguarding the privacy and security of employees and sensitive business data. Below are some things to keep in mind:
- Data Protection and Privacy Laws: The Personal Data Protection Act (PDPA) governs how personal data, including biometric information, is collected, used, and stored. Businesses using biometric systems, such as fingerprint or facial recognition technology, must follow PDPA guidelines. This includes obtaining consent from individuals and storing their data securely.
- Building and Safety Codes: Access control systems must comply with all relevant building and safety regulations to avoid legal complications. For example, hardware installation should not interfere with fire safety systems or violate occupancy laws.
- Industry Standards: Businesses in healthcare, finance, or education sectors may face additional regulations regarding access to sensitive data or restricted areas. Additionally, check that the system meets industry-specific standards, such as ISO 27001 for information security.
3.3.2 Keeping Up-to-Date with Technology
As access control technology evolves, businesses should choose systems that can adapt to new developments and future needs. Some effective strategies include:
- Support for New Technologies: Choose systems that integrate with emerging technologies, such as Artificial Intelligence (AI), the Internet of Things (IoT), and cloud-based solutions. For example, AI-driven analytics can identify potential security threats by analysing usage patterns and access anomalies.
- Upgrade Paths: Select systems that allow easy upgrades to give businesses the flexibility to adopt new features over time. This could involve software updates, hardware upgrades, or adding new access methods like voice recognition or mobile-based authentication. Cloud-based solutions typically offer greater scalability and remote updates without complex on-site installations.
- Regular Reviews and Performance Assessments: Periodic reviews of the system’s performance help evaluate factors like efficiency, security effectiveness, and user experience. This proactive approach allows businesses to identify areas for improvement and make adjustments as necessary.
3.3.3 Future Trends in Door Access Management
Staying ahead of emerging trends ensures businesses are prepared for both current and future security challenges. Here are some trends to watch out for:
- Advancements in Biometrics: Biometric technology continues to evolve, with new methods like multi-factor biometric authentication, combining multiple identifiers for enhanced security. More accurate, non-intrusive systems, such as palm vein scanning or voice recognition, may offer both increased security and greater user convenience.
- IoT Integration: As smart office solutions become more common, access control systems are increasingly integrated with IoT devices, such as smart locks, sensors, and AI-powered cameras. This integration enhances operational efficiency, allowing businesses to manage security in real time and make adjustments when needed.
- Cloud-Based Solutions: Cloud technology provides scalability, easier management, and remote access. Businesses can scale their security systems more efficiently and receive updates and integrations without the complexity of traditional on-site systems.
- AI-Driven Analytics: AI can analyse user behaviour and access patterns to identify unusual activity that could indicate security threats. Predictive analytics might help businesses anticipate security incidents and take action before problems escalate, offering a more proactive approach to security.
Complying with regulations and future-proofing access control systems helps enhance both security and operational efficiency. By staying informed about emerging technologies, businesses can create a secure, scalable, and future-ready security environment.

Frequently Asked Questions
Here are answers to some common questions about door access systems:
1. Can biometric access control systems be used outdoors?
Biometric systems like fingerprint or facial recognition can be used outdoors with proper environmental protection and considerations for weather conditions. Outdoor-rated biometric devices are available to withstand elements like rain and humidity.
2. What should I do if an employee loses their access card or forgets their PIN?
Immediately deactivate the lost access card or change the PIN to prevent unauthorised access. To maintain security protocols, you must have a streamlined process for reporting and replacing lost credentials.
3. How do office door systems handle power outages or emergencies?
Many office door access systems are designed with backup power options, such as battery backups or uninterruptible power supplies (UPS). These systems often have fail-safe modes to ensure continuous operation and security in emergencies.

The right door access control solution is essential for boosting office security and improving operational efficiency. As technology evolves, staying updated with the latest advancements in door access management is crucial. With the right system in place and proper maintenance, you can protect your premises while enjoying the added convenience and functionality these systems offer.
At iDLink Systems, we recognise that every business has distinct security needs. That’s why we offer custom, integrated access control solutions tailored to your specific requirements. Whether you need biometric systems, smart locks, or a complete security ecosystem, our expertise will help you select and implement the perfect solution.
Contact us today to schedule a consultation and explore how our innovative, bespoke access control solutions can meet your security goals. Let us help you protect your office and stay ahead with the latest advancements in access control technology.



